What are Phishing Attacks?
Phishing attacks are designed to trick you into revealing sensitive information or installing malware (including ransomware) on your devices. They are carefully crafted to look genuine and appear, on the surface, to be from a legitimate source.
Phishing methods
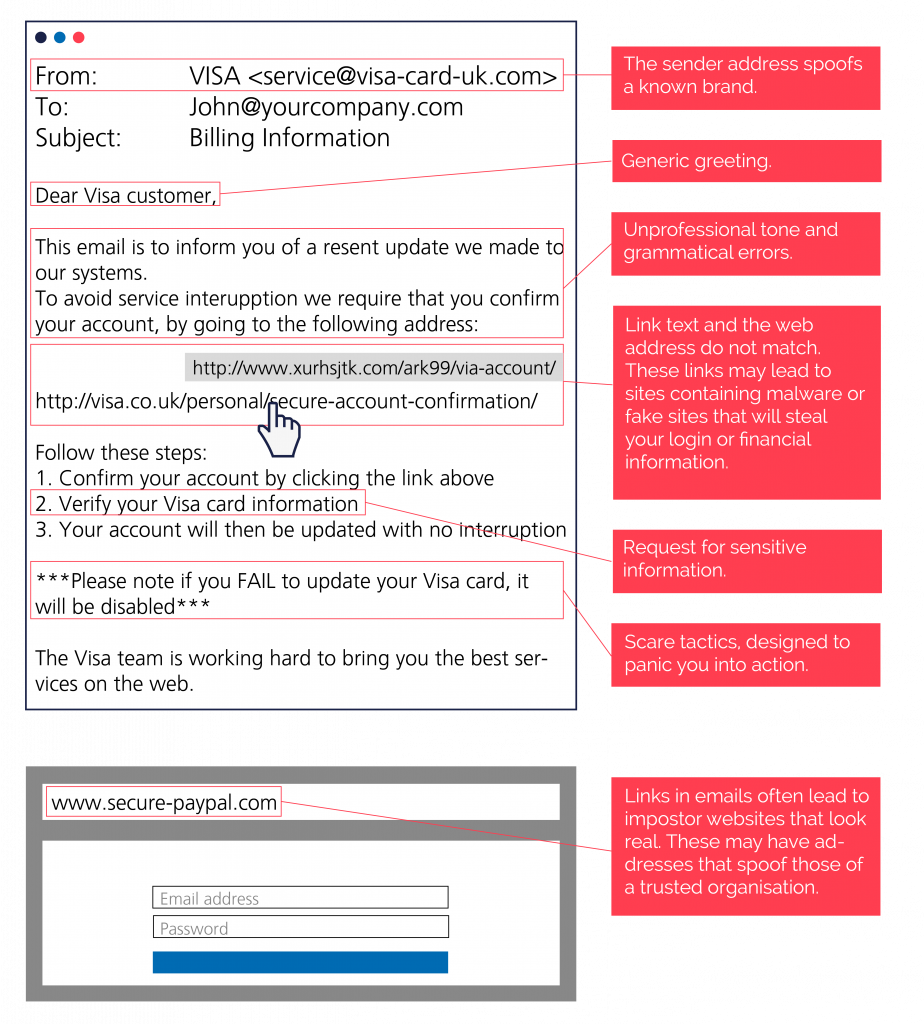
Mass Phishing: The most common type of attack, using little personalisation. These emails usually appear to come from a recognised service provider, like a bank or HMRC and are cast out to a huge amount of email addresses.
Spear Phishing: A targeted attack which uses found or stolen information to tailor an email for an individual or group in order to make it more convincing.
Whaling: A personalised attack aimed at figures of authority in a company, with the goal of stealing their login information. This can then be used to impersonate the individual and authorise or direct fraudulent payments.
Phishing emails 📧
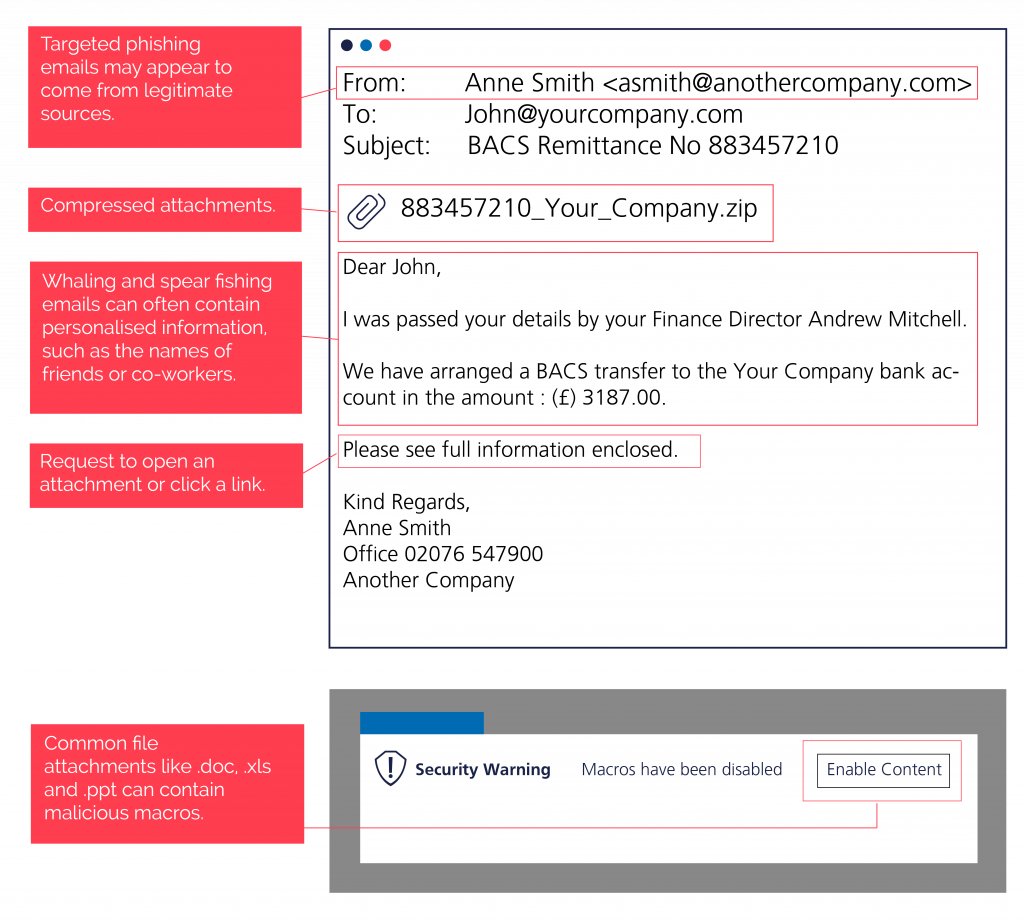
Phishing emails can often look convincing initially, but there are some tell-tale signs to look out for:
Targeted Phishing Emails 📧
Targeted phishing emails can also appear to come from colleagues, suppliers and other close business contacts.
Common Phishing Emails:
Here are some of the most common phishing emails we see:
- OneDrive file share links – this also extends to Google Docs and Dropbox
- Password update requests
- Unusual activity on your account
- Multi-factor authentication set up (typically ‘from’ Microsoft)
- Requests for payment / fake invoices
- Messages from HR teams
- Account upgrades
- Free advice
Vishing 📞
Voice phishing is referred to as Vishing. Criminals make telephone calls to gain access to private and financial information.
- The caller will already have genuine information like your name, address, phone number and bank details.
- Criminals will create a sense of fear and urgency – often that your money is in danger and you need to act quickly.
- Fraudsters sometimes offer unsolicited prizes or present offers that are too good to be true.
- The phone number may be spoofed so it looks like the call is coming from a legitimate source.
- Criminals can sometimes hold your telephone line, so if you hang up and call again on the same line, you might get put straight back through to them.
- There may be fake background noise to make it appear as if the call is coming from a call centre.
If you receive a suspicious phone call, hang up. Search for the apparent callers details on their website or on official documentation, and call them back on a different device to confirm if the call was real.
If you get an unexpected call from your bank, you can hang up and dial 159. You will safely be connected to your bank, and 159 cannot be spoofed.
Smishing 📱
SMS phishing is similar to email phishing, but uses text messages. As with vishing and spear phishing it can be personally targeted.
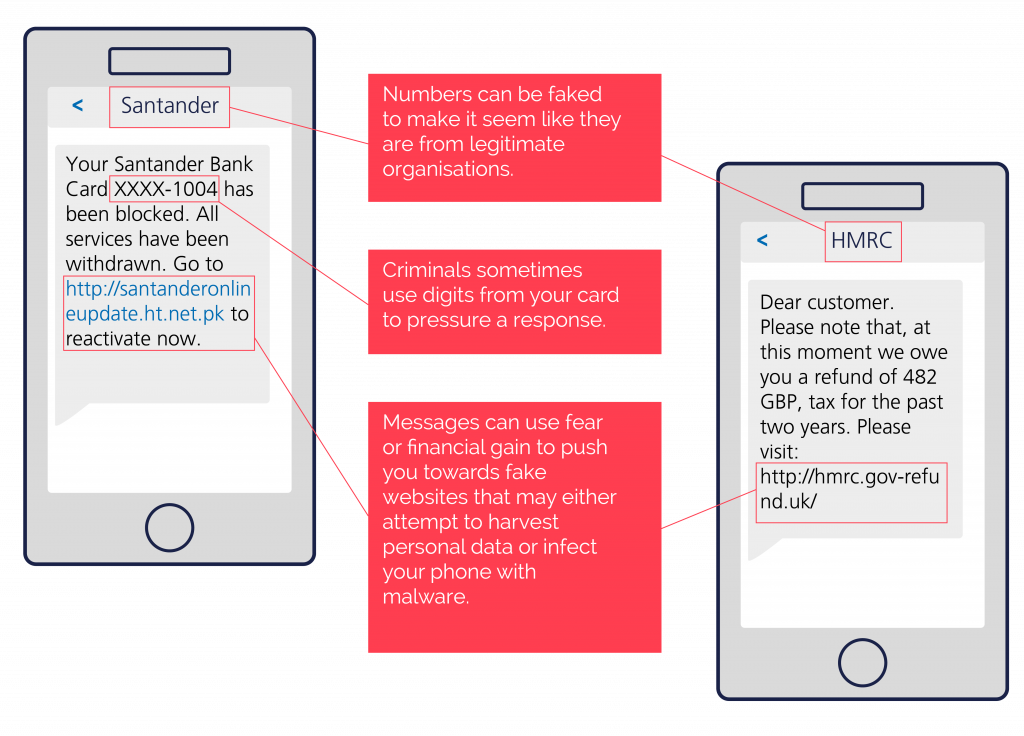
If you receive a scam SMS, you can report it by forwarding the message to 7726 for free.
Quishing 🤳
Quishing is phishing using QR codes. QR code scams are popular because you use your mobile phone which typically has less protection than your laptop.
Offline:
There are two things to consider with QR codes in the physical world:
1) Is the QR code attached to a legitimate source?
2) Has the QR code been replaced?
Examples:
1) A fake event flyer created to generate sign up with financial information through a QR code.
2) A malicious QR code sticker has been placed over the one you would scan to pay for your car parking.
Online:
Online, QR codes are often used to encourage app downloads, verify accounts and more.
Criminals will replicate emails, or put out malicious QR codes in the hope that you will scan them and follow any
instructions required.
Don’t scan any QR code if you can’t confirm the source. Instead, search for the information in your browser or contact the sender to confirm.
Social Media Phishing 👀
Criminals use social media to launch attacks that aim to steal personal data, spread malware or even hijack accounts.

Criminals set up replica accounts to contact the victim’s followers to tell them that their legitimate account has been abandoned. They will then send messages from the new account to try and trick the victim’s followers into clicking on links to websites which may steal data or contain malware.
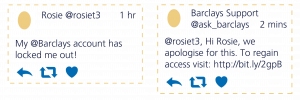
In ‘angler phishing’ attacks, scammers steal branding and create fake customer service accounts. These are then used to respond to genuine user support requests, directing them to legitimate looking but fraudulent malicious websites.

Scammers will also attempt to imitate website admins with the aim of tricking people into giving up passwords and other sensitive information.
![]()
On LinkedIn, criminals will set up fake profiles to send connection requests and attempt to message you, which ultimately will turn out to be a scam.
Before you accept a connection request, check the full profile. Pay attention to their work and education history, as well as incomplete information. The best solution: don’t accept the request if you don’t know them.
How to Stay Safe 🔐
Zero Trust
Adopting a zero trust strategy literally means trust nothing. You should validate the source of every email, SMS, telephone call etc., before you take action.
Don’t click on links or download attachments
Don’t engage with anything in the communication until you have confirmed it is safe to do so.
Contact the sender directly
Use details on the apparent sender’s official website and documentation to try and confirm legitimacy of the contact. If you are contacted on a phone, try to use a separate device to get in touch in case the line is being held.
Be suspicious
Look carefully at any unsolicited communication, particularly if it encourages you to take urgent action or it seems out of character for the sender.
Report any suspected phishing activity
At work, take the below steps if you receive or action a phishing email:
You received a phishing email:
1) Do not action the phish. Take a screenshot of the email and send this to all of your colleagues.
2) Contact us to report the suspected phishing activity. We can then take action, including removing the email from all user mailboxes.
You clicked a phishing email
1) Contact us immediately to let us know. We can then take action and check for any further incidents.
2) Let the appropriate person within your organisation know. This could be a senior manager or internal IT support.
On your personal device, please contact Action Fraud at: www.actionfraud.police.uk
What is Phishing?
Phishing is a form of cybercrime which targets victims by email, SMS or telephone. Criminals will pose as legitimate organisations to trick you into revealing sensitive data, such as bank details or passwords. This then results in identity theft or financial loss.
What is Ransomware?
Ransomware is a type of infectious software designed to prevent you from accessing your files, databases, and applications until a request is fulfilled; this is typically a payment to the attacker.
What is Zero Trust?
Zero trust is a strategic approach used by organisations. It includes both employee attitude and security policies put in place, encouraging employees to validate every action they take.