In celebration of Cyber Security Awareness Month each October, we’ve put together a list of 31 cyber security tips – one for each day of the month!
Tip 1
Adopt a zero-trust strategy to protect yourself from phishing attempts. By doing so, you question the legitimacy of every email, phone call, website etc. You may also implement policies to restrict data access. Learn more.
Tip 2
If USB sticks can be difficult to track. Consider using alternative methods of file sharing such as email or via the cloud. you need to use USBs in your organisation, install USB blocking software to label certain drives as safe to access (pssst, we can help with this!).
Tip 3
Make sure that you keep your apps and software up to date. If you can, turn on automatic updates. Updates often contain security patches. Ignoring these will leave you vulnerable.
Tip 4
Enable multi-factor authentication (MFA) on ALL your accounts. MFA apps are free. And you can list devices as secure, meaning you don’t have to put in the MFA code every time you log in on a certain device. Learn more.
Tip 5
If you receive a suspicious-sounding call, hang up immediately. To validate the call, don’t call back the number that called you. Instead, go to the company’s website and call the number listed there. Be aware that scammers can keep your telephone line open. Wait to make calls, or use a different device.
If you get an unexpected call from your bank, you can hang up and dial 159. You will safely be connected to your bank, and 159 cannot be spoofed.
Tip 6
Make sure your backup is tested regularly to ensure that it is working properly. We’d recommend testing your backup every one to three months.
Tip 7
When setting a new password, make it secure by using three random words and a mix of characters.
Tip 8
Never leave a device unattended, even if it’s locked (that includes in your favourite coffee shop whilst popping to the loo). It’s not just about stealing the actual device anymore. Criminals could plug in a USB and infect your device in seconds.
Tip 9
Struggling to understand the jargon used in cyber security? Then download our cyber security glossary! It covers the key terminology used from antivirus to whaling. Download now.
Tip 10
If you’ve received an email with a link in the body text, hover your mouse over the link. The actual web address will appear, meaning you can check the legitimacy of the link before risking a click.
Tip 11
Become Cyber Essentials Certified! Being certified ensures that you have the essential level of protection in place and demonstrates a commitment to cyber security. Learn more.
Tip 12
Getting employees to change their passwords regularly doesn’t necessarily make them more secure. Most will just change a letter or number. Use multi-factor authentication and password managers to secure their accounts properly.
Tip 13
Don’t just assume that cyber security attacks happen remotely. Criminals may use tactics to get into your offices, plug in malicious USB sticks or even leave them lying around, hoping an employee will plug them in.
Tip 14
Get your staff to do regular security awareness training. This doesn’t have to be full-day, classroom-style sessions. We can provide you with regular, fun, two-minute videos to help keep on top of the latest threats. Let us help!
Tip 15
Don’t use public Wi-Fi. Hackers can position themselves between you and the connection point. That means your data is being sent directly to the hacker.
Tip 16
Be careful about what information you share on your social media sites – including LinkedIn, Instagram, Twitter etc. Cyber criminals may use this information to guess passwords, or even find behaviour patterns.
Tip 17
Make sure the websites you are visiting are secure by looking for the ‘https’ in the URL. You may also see a padlock icon to the left of your URL bar.
Tip 18
Implement bring your own device (BYOD) policies. Policies implemented will protect your business if employees access company data on personal devices e.g. mobiles. Learn more.
Tip 19
Received a file share email from a colleague? Pause. Question whether you were expecting this from them. Contact them directly to confirm if the email is from them before opening anything. This is a common phishing tactic.
Tip 20
Upgrade from antivirus to endpoint detection and response (EDR). Antivirus is no longer enough to keep you safe from modern cyber threats. EDR detects threats faster and can put a stop to any malicious behaviour. Learn more.
Tip 21
Switch off auto connection on devices. You could accidentally create a malicious connection via open wireless networks or Bluetooth.
Tip 22
Make sure your hardware (laptops, mobiles, PCs, etc.) is kept up to date. Ageing devices may stop receiving software updates, making them vulnerable to attacks.
Tip 23
Password don’ts:
- Don’t reuse a password
- Don’t use a pet name
- Don’t use your birthday
- Don’t use your favourite sports team
- Don’t use keyboard patterns (qwerty)
- And definitely DON’T use password as your password
Tip 24
Penetration testing should ideally be carried out every year. Pen testers attempt to breach your organisation using the same tools and techniques as real hackers. This gives you a real-world overview of your security. We offer pen testing as a service.
Tip 25
Phishing can happen on social media. An example of this is a profile impersonating a company’s support account and requesting details from you. If you’re suspicious, contact the company directly using details on their website.
Tip 26
If you’re allowing clients or customers to access Wi-Fi on your premises, make sure you set it up as a guest network. A guest network gives visitors access to the internet and nothing more.
Tip 27
If you receive a phishing email, forward it to: report@phishing.gov.uk. They will check the email and take down any malicious sites.
Tip 28
Use a password manager for your work and personal accounts. It’s a great way to securely store, generate and manage your passwords and other sensitive information. Learn about our partnership with LastPass.
Tip 29
If you receive a suspicious text message, forward it to 7726. They will check the legitimacy of the message and block the sender if found to be malicious.
Tip 30
Be wary of any emails, text messages or phone calls pressuring you for immediate action. Always check the communication by contacting the ‘sender’ direct using a contact method from a legitimate source.
Tip 31
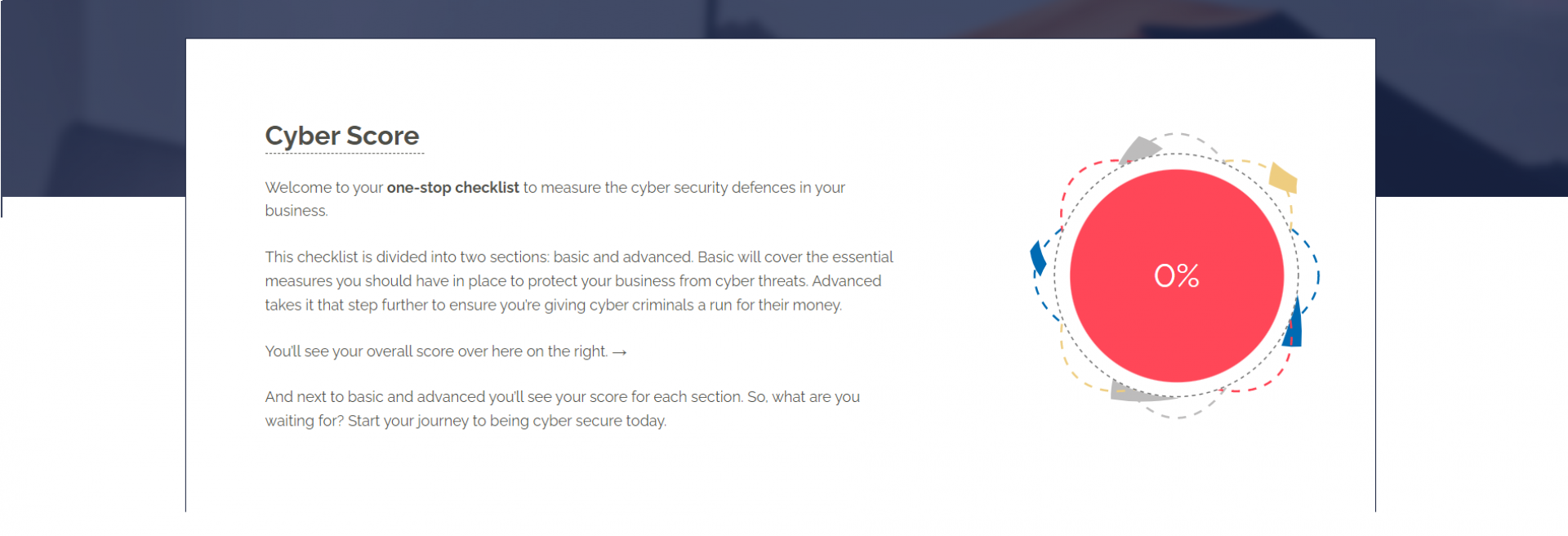
(Shameless plug incoming…) Use Cyber Score! It’s a free, do-it-yourself checklist that allows you to score the cyber security measures you have in place within your organisation.